
Beware of a New Email Scam Targeting WordPress Website Owners.
A new phishing email scam has emerged, targeting WordPress website owners with very deceptive tactics. The scam involves an email that warns site owners of a supposed security vulnerability and urges them to download and install a plugin to address the issue. However, this email is not legitimate and threatens the security of WordPress sites. Website owners must be aware of some red flags associated with this scam to protect themselves and their websites.
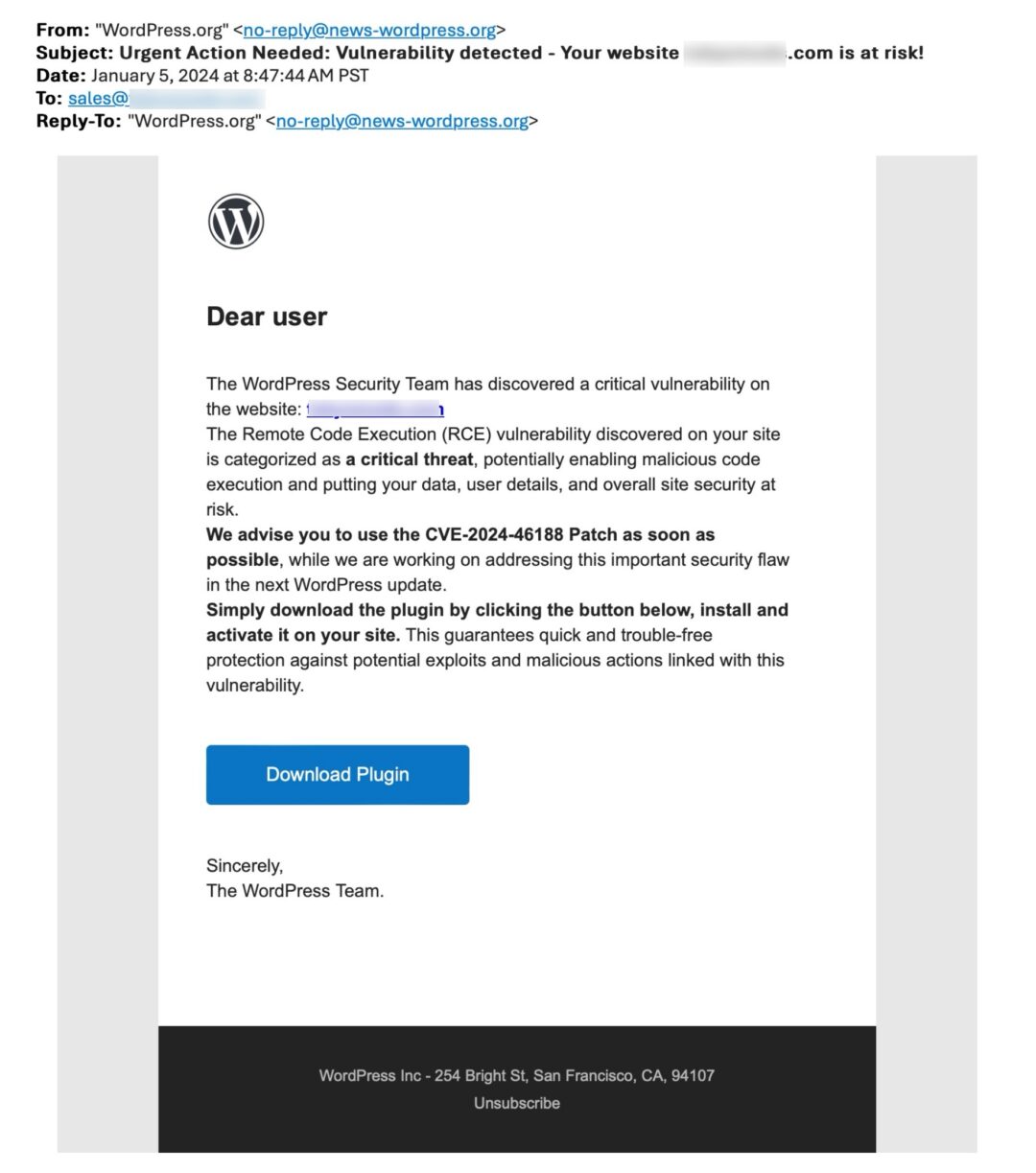
Deceiving Phishing Patch CVE-2024-46188 Email
You should always review your emails carefully before you trust them! You will notice that this email came from no-reply@news-wordpress.org
WordPress will not send you emails from news-wordpress.org. Nor will they direct you to a plugin outside of their repository, which is located wordpress.org/plugins
This email advises you to download and install a plugin for a WordPress security patch CVE-2024-46188.
QUOTE FROM EMAIL: “We advise you to use the CVE-2024-46188 Patch as soon as possible, while we are working on addressing this important security flaw in the next WordPress update.
Simply download the plugin by clicking the button below, install and activate it on your site.”
By installing this plugin, Ram Gall from WordFence states:
“This allows attackers to maintain persistence through multiple forms of access, granting them full control over the WordPress site as well as the web user account on the server.
Indicators of Compromise:
- A wp-autoload.php file in the webroot with a SHA-256 hash of ffd5b0344123a984d27c4aa624215fa6452c3849522803b2bc3a6ee0bcb23809
- A plugin with a slug of wpress-security-wordpress
- A hidden administrative user with a username of wpsecuritypatch
- The following malicious domains:
- en-gb-wordpress[.]org
- wpgate[.]zip“
Over the years we have been working on WordPress, we have never received a notice where the WordPress core was compromised and to install a plugin. And if it was that critical WP would have released a Core update or inserted a notice within the admin.
What happens if you receive an email such as this?
- Verify the source of truth, and DO NOT click on the link.
- If you insert CVE-2024-46188 into the search on WordPress, a few articles will be displayed.
- Perform a Google search using the “vulnerability patch CVE-2024-46188”
- Try to locate the plugin within WordPress.
- If you download and install this plugin, the site will be compromised, and the attackers can steal sensitive data from your website.
Play it safe, not sorry!
Check the source of truth!
Sign-up and receive security emails from:
- WordFence is another great truth of source. In the footer you can sign uop for their newsletter. Here is a great article on this Phishing Scam
Suggestions
- Always back up your site before you perform any update on it.
- Ensure you have strong Passwords and change them regularly.
- Scan your site https://sitecheck.sucuri.net/wordpress-malware-scanner/
If you are not using Kinsta as your host provider, I strongly recommend it.
Backups are simple, and if you want, you can create a staging environment, they are included within their affordable price.
Kinsta’s offers speeds that rock like no other provider!